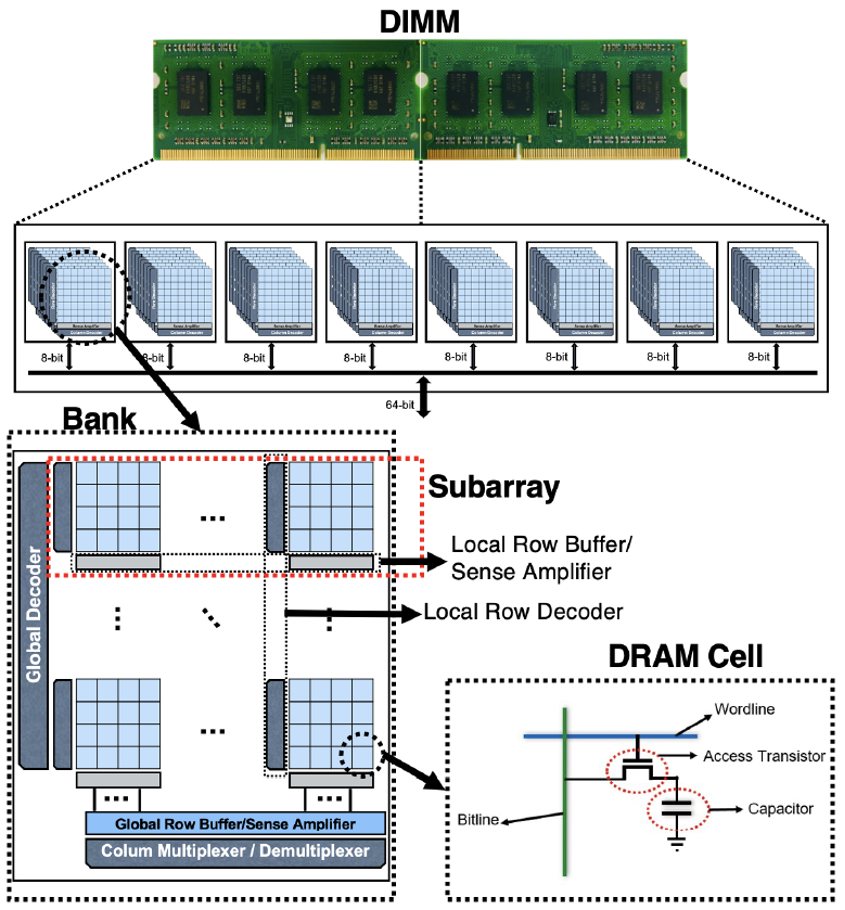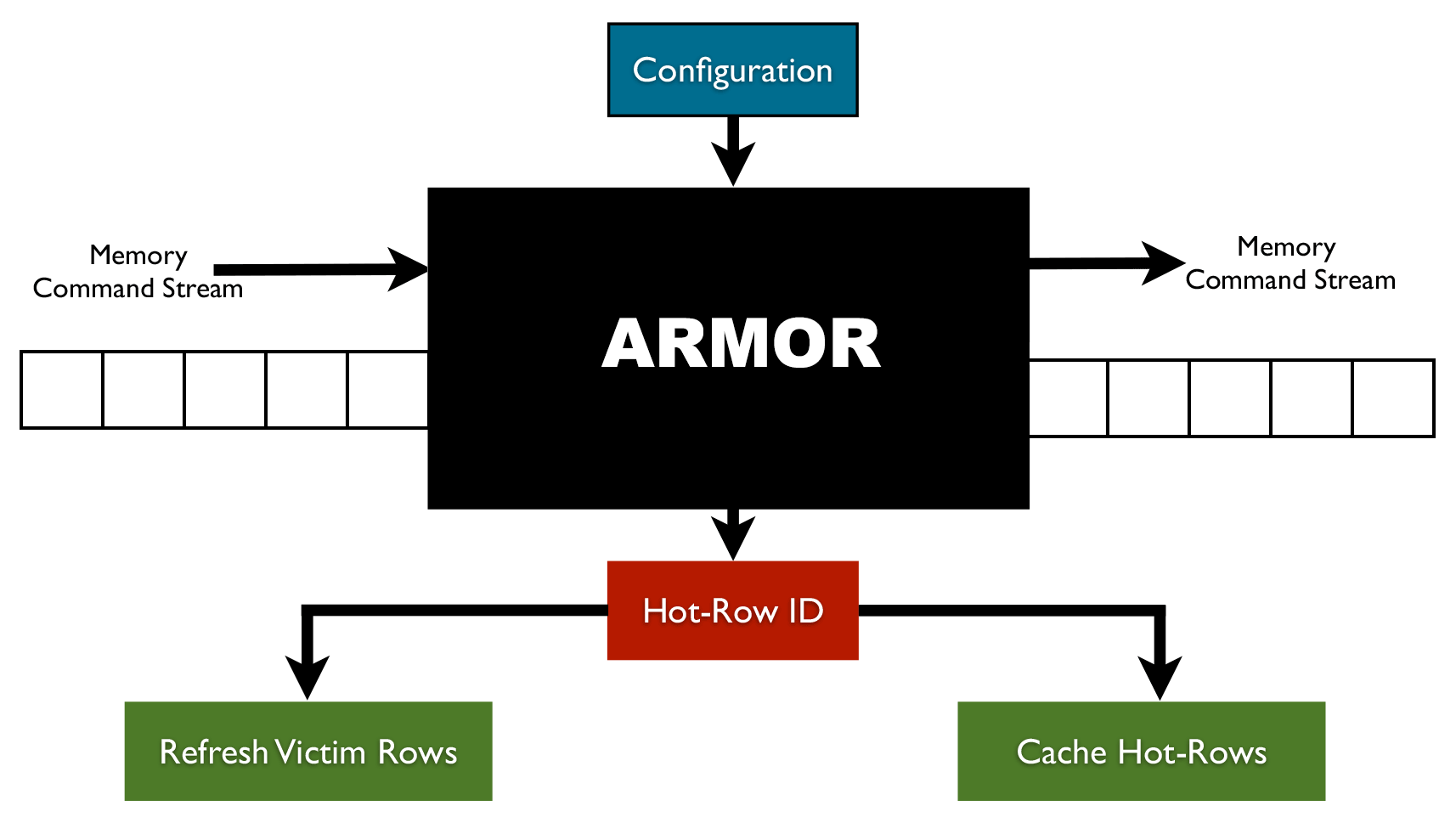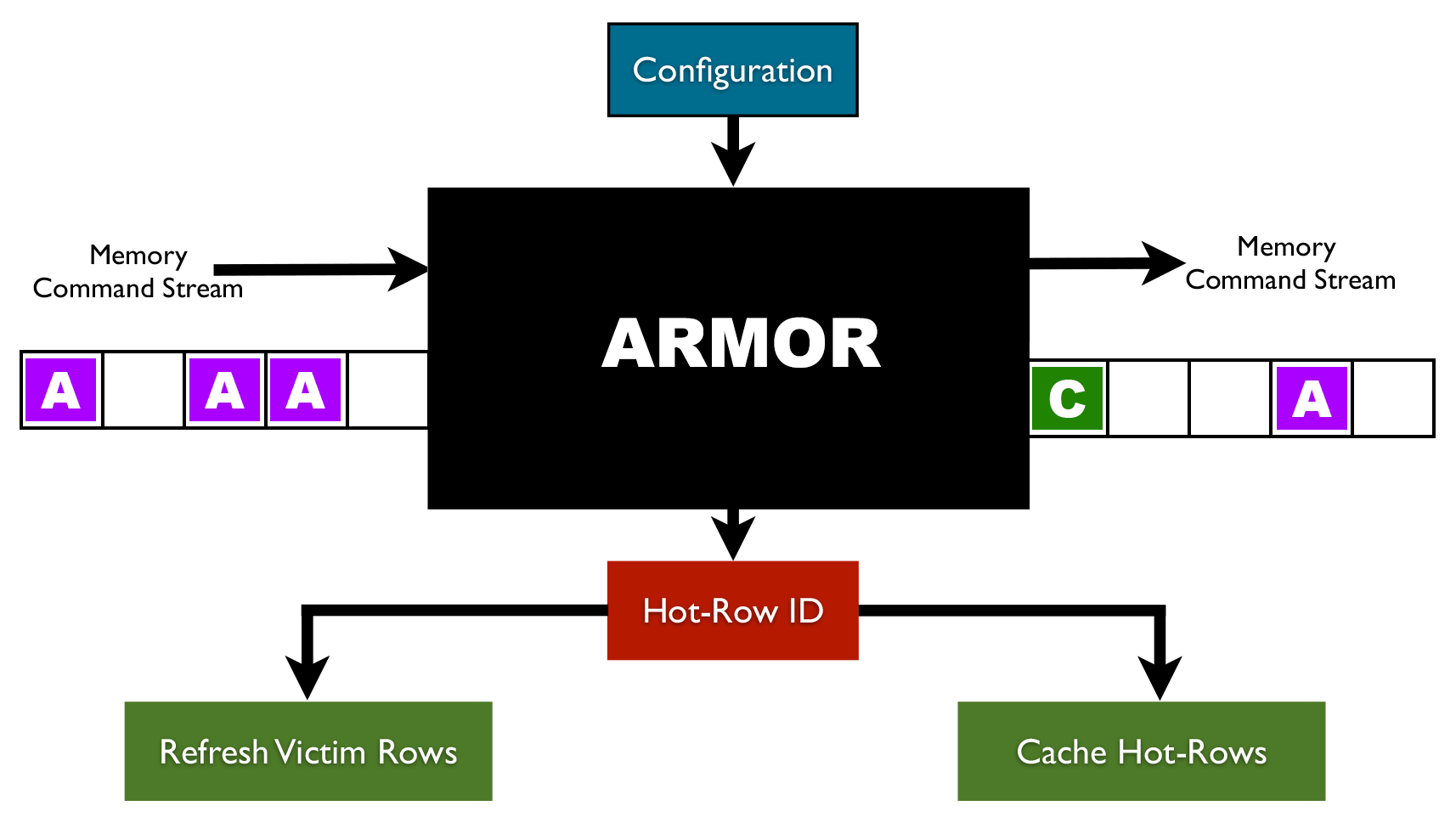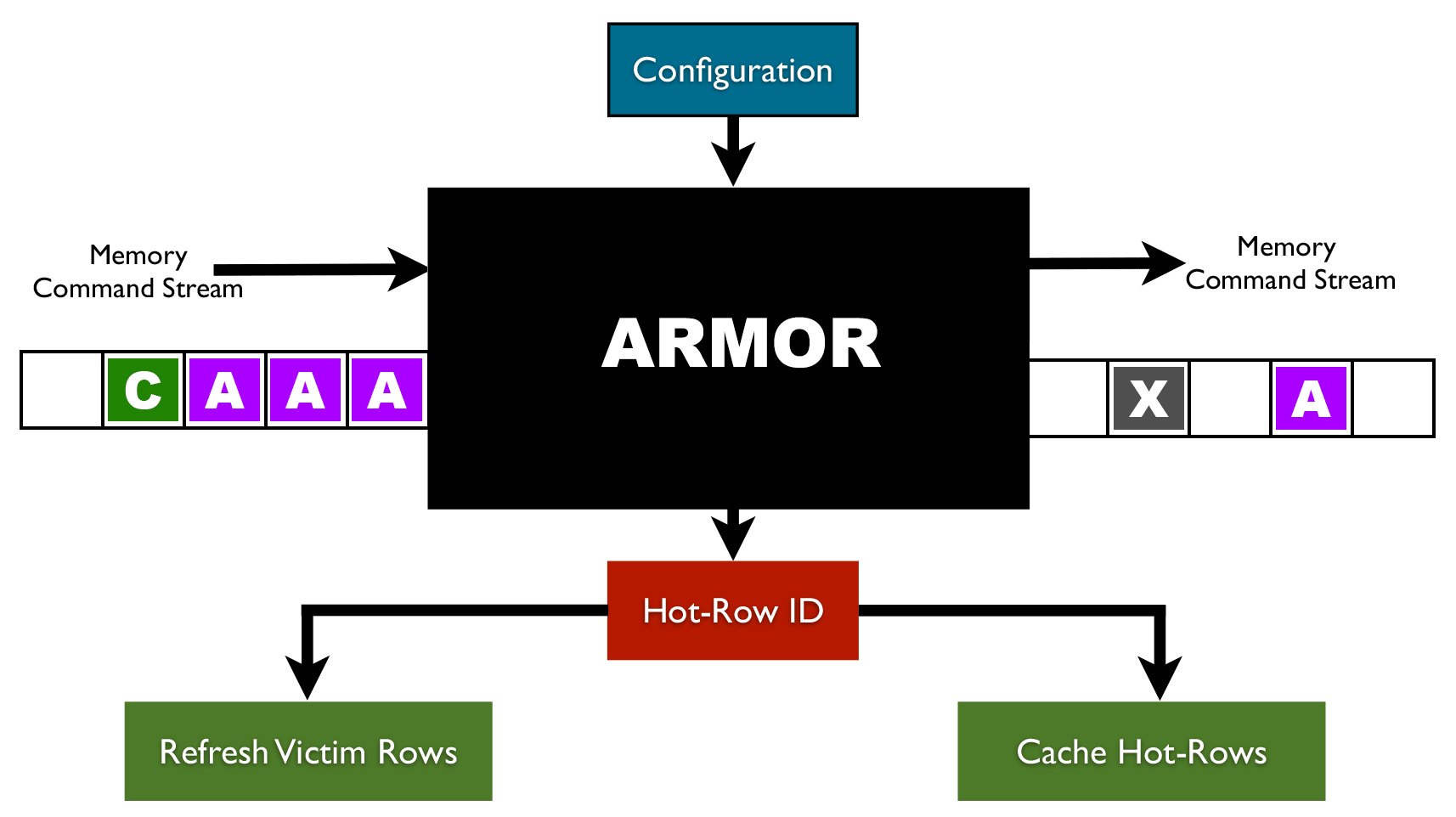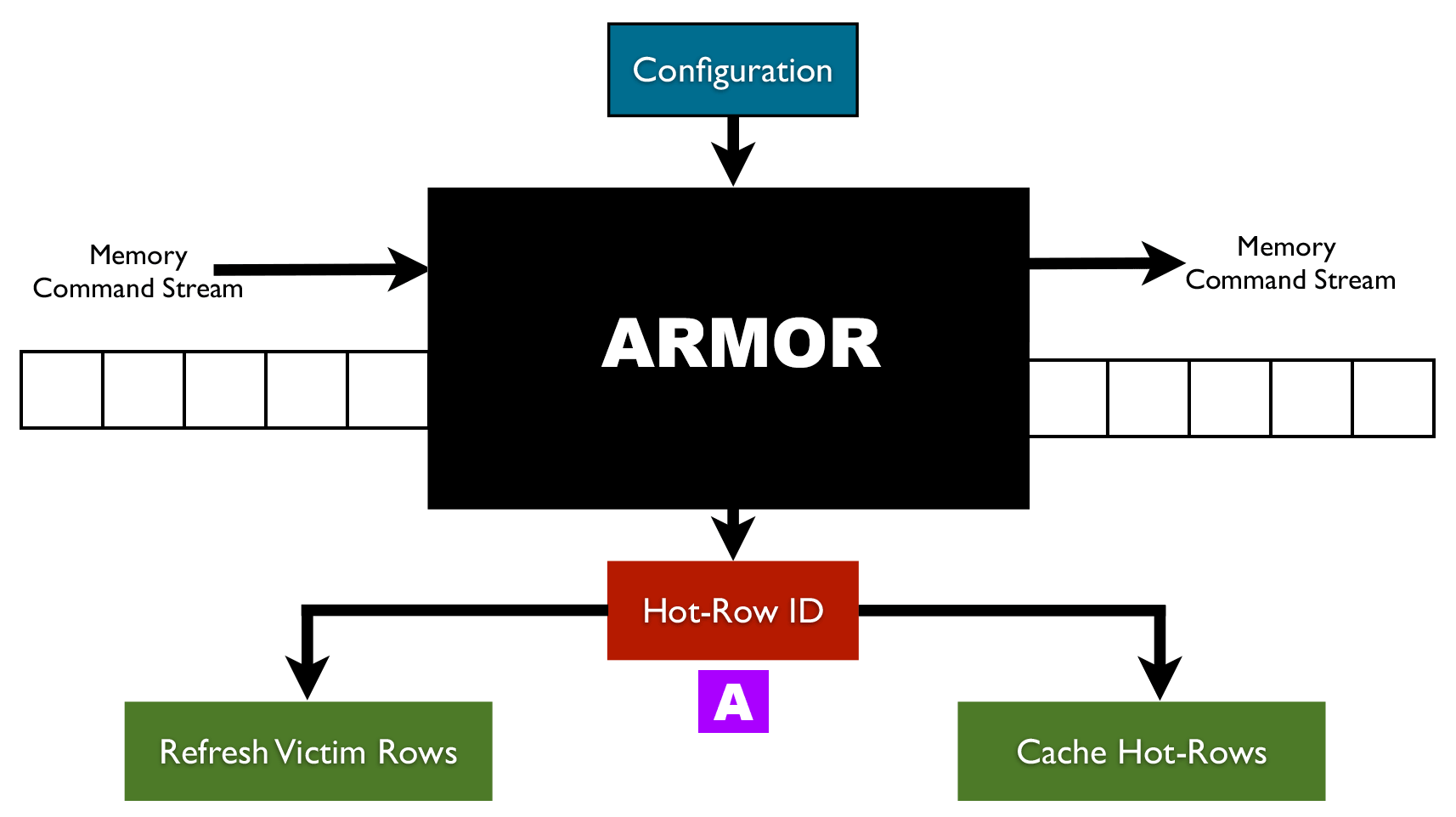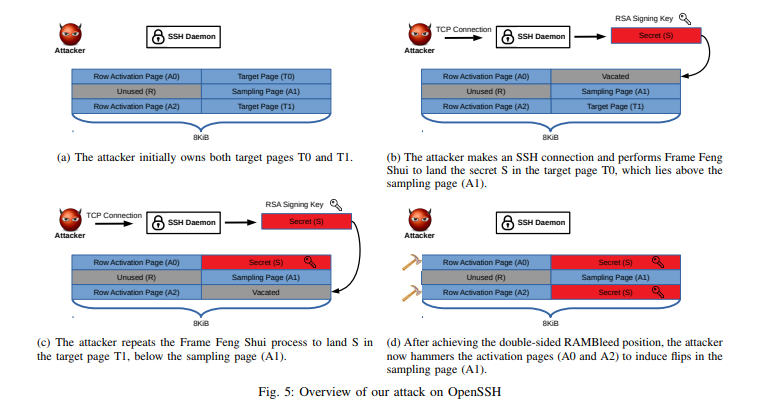
RAMBleed: A Rowhammer-based side-channel attack that reads memory bits without accessing them - Security Boulevard

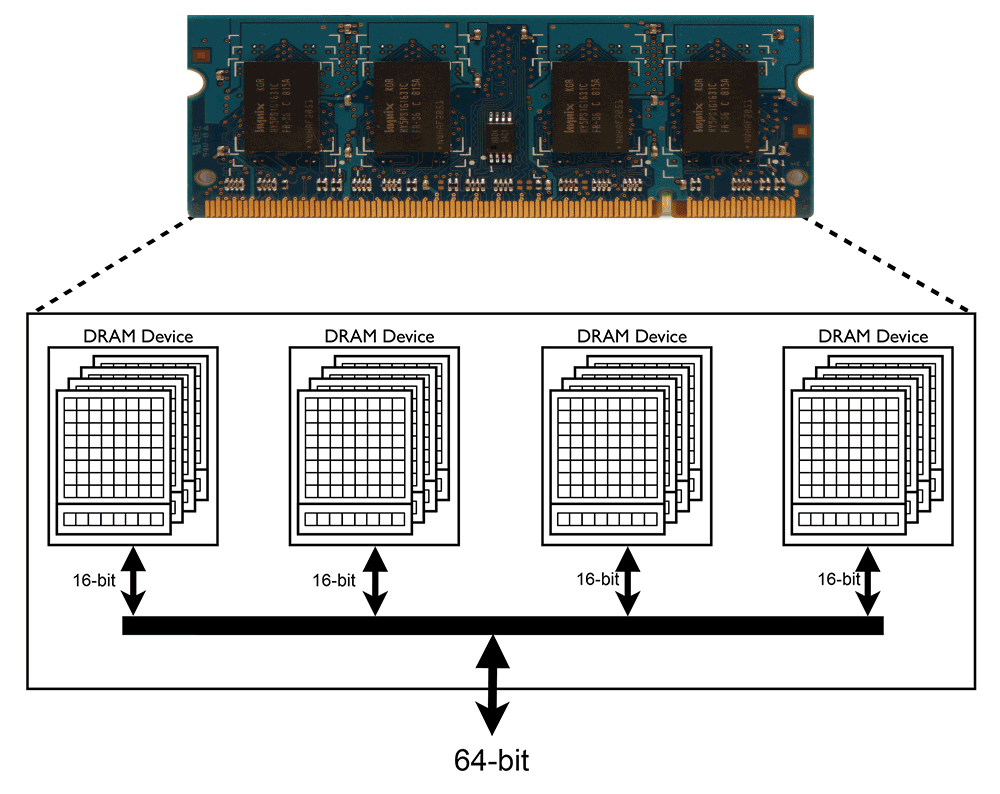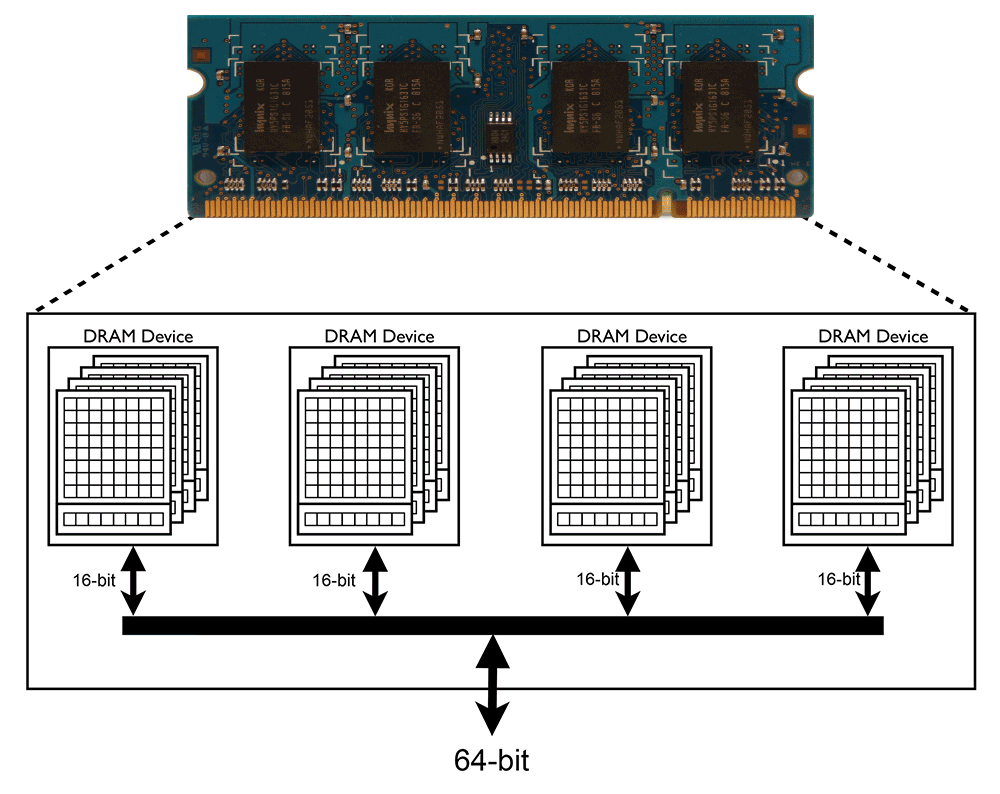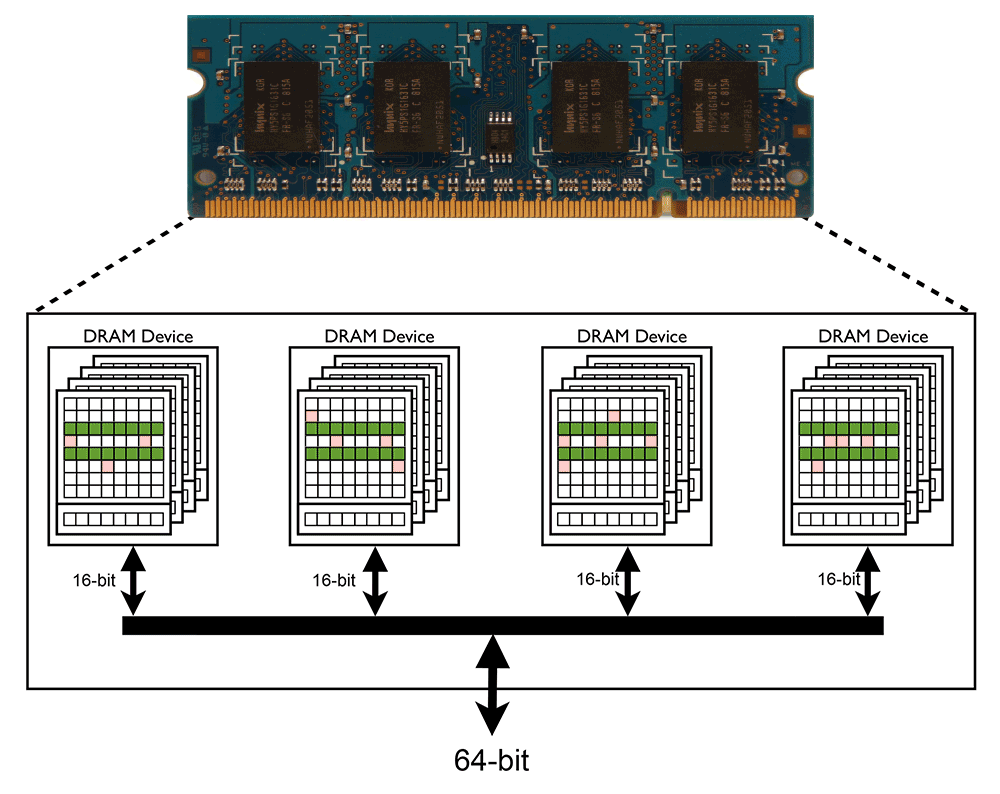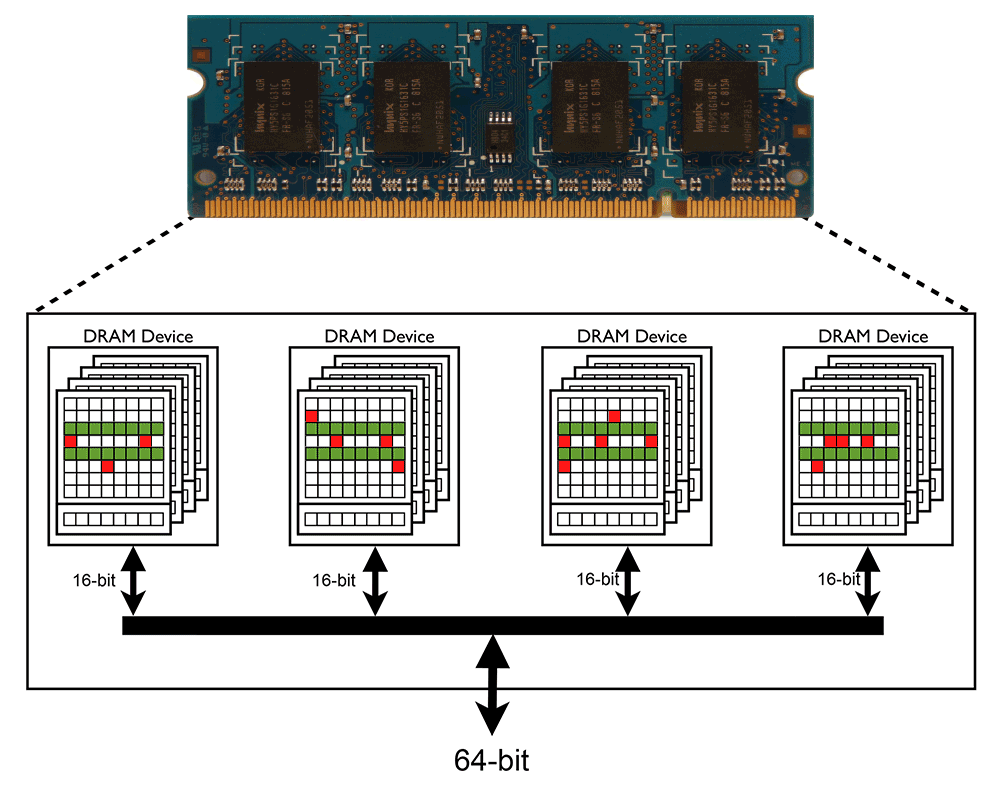
Suppression of Row Hammer Effect by Doping Profile Modification in Saddle-Fin Array Devices for Sub-30-nm DRAM Technology | Semantic Scholar

Row Hammering types: (a) Double-Sided Row Hammering (DSRH) with PUF... | Download Scientific Diagram
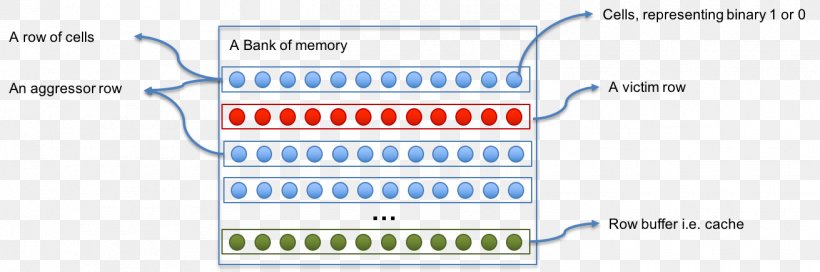
Row Hammer Exploit Android Computer Security Computer Software, PNG, 1311x435px, Row Hammer, Android, Area, Bit, Brand

Suppression of Row Hammer Effect by Doping Profile Modification in Saddle-Fin Array Devices for Sub-30-nm DRAM Technology | Semantic Scholar